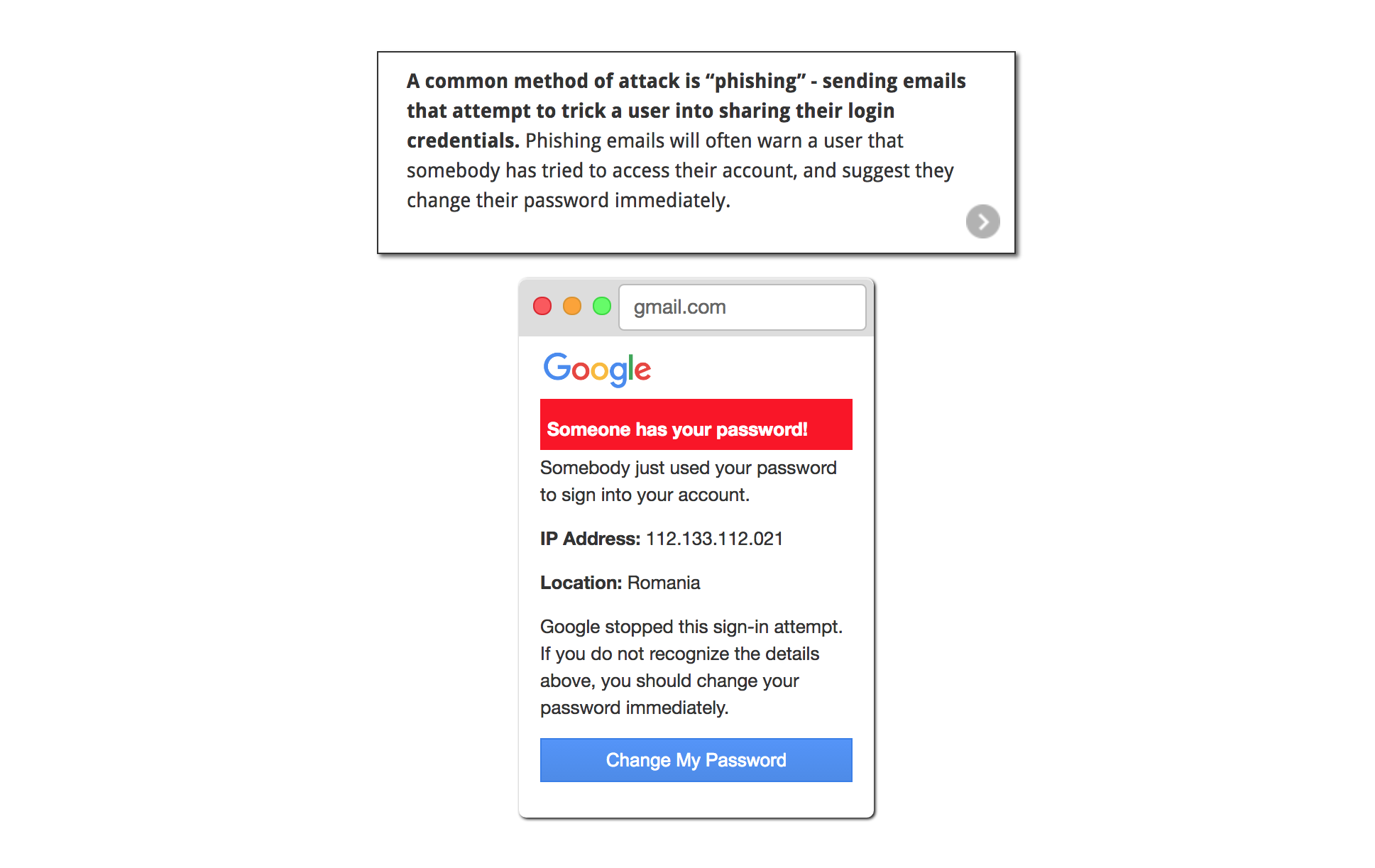
What is the best defense against email spoofing?
Implement Domain Key Identified Mail (DKIM): use a digital signature to prove that outgoing email was legitimately sent from your domain, and that it wasn't modified in transit.
What are the protections against email spoofing?
Mitigating the risk posed by email spoofing requires a multi-layered approach to security. Security awareness training can help users to more easily spot and avoid email spoofing attempts. Email filters that use DNS authentication services like SPF, DKIM and DMARC can help to lock potentially fraudulent email.
Can you prevent spoofing?
Website spoofing uses domain names, logos, and colors that imitate real sites. Once victims are hooked, spoofing employs social engineering to convince them to divulge sensitive information or transfer funds. Cybersecurity training and automated email authentication are key to preventing spoofing attacks.
How do you protect email display name spoofing?
You can use email authentication protocols like SPF and DMARC to avert them. SPF or Sender Policy Framework uses a list of IP addresses authorized to send emails using your domain, while DMARC instructs recipients' mailboxes on how to treat unauthorized emails coming from your domain.
How do firewalls protect against email spoofing attacks?
Install a Firewall Upon detecting a spoofed email address, spoofed IP address, or spoofed website, your firewall prevents the dangerous message from reaching your computer or local area network (LAN).
What are the protections against email spoofing?
Mitigating the risk posed by email spoofing requires a multi-layered approach to security. Security awareness training can help users to more easily spot and avoid email spoofing attempts. Email filters that use DNS authentication services like SPF, DKIM and DMARC can help to lock potentially fraudulent email.
What is email spoofing?
Email Spoofing Definition Email spoofing is a threat that involves sending email messages with a fake sender address. Email protocols cannot, on their own, authenticate the source of an email. Therefore, it is relatively easy for a spammer or other malicious actors to change the metadata of an email.
What threats is the Anti-Spoofing protecting from?
Anti-spoofing Prevent payload-less attacks such as spoofing, look-alike domains, and display name deception with unmatched precision through machine-learning algorithms with IP reputation, SPF, DKIM, and DMARC record checks.
How is anti spoofing done?
Anti-Spoofing detects if a packet with an IP address that is behind a certain interface, arrives from a different interface. For example, if a packet from an external network has an internal IP address, Anti-Spoofing blocks that packet.
What are 3 common types of spoofing?
Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What can you do about spoofing?
If you think you've been the victim of a spoofing scam, you can file a complaint with the FCC. You may not be able to tell right away if an incoming call is spoofed. Be extremely careful about responding to any request for personal identifying information. Don't answer calls from unknown numbers.
Does Gmail protect against email spoofing?
Authentication helps prevent messages from your organization from being marked as spam. It also prevents spammers from impersonating your domain or organization in spoofing and phishing emails.
Can a spoofed email be traced?
If a spoofed email does not appear to be suspicious to users, it likely will go undetected. However, if users do sense something is wrong, they can open and inspect the email source code. Here, the recipients can find the originating IP address of the email and trace it back to the real sender.
Does SPF prevent email spoofing?
SPF is a standard email authentication method. SPF helps protect your domain against spoofing, and helps prevent your outgoing messages from being marked as spam by receiving servers. SPF specifies the mail servers that are allowed to send email for your domain.
How do firewalls protect from hackers?
A firewall can help protect your computer and data by managing your network traffic. It does this by blocking unsolicited and unwanted incoming network traffic. A firewall validates access by assessing this incoming traffic for anything malicious like hackers and malware that could infect your computer.
Does firewall protect emails?
How firewalls work. Email firewalls are set up to protect individuals or complex networks. They filter incoming and outgoing email-server traffic based on a set of rules determined by the firewall administrator.
Does VPN prevent spoofing?
DNS Spoofing (DNS Poisoning) VPNs can keep you safe from DNS poisoning by encrypting your DNS requests and good providers like ExpressVPN and NordVPN even handle them through their own DNS servers (read our ExpressVPN review).
Why can't they stop phone number spoofing?
As mentioned earlier, there are some instances where spoofing is legal. And since the phone companies can't tell what's legal and what's not, they cannot stop it.
Does VPN help with spoofing?
VPNs are often used to spoof the user's location and access region-locked content and services. It does this by routing the device's VPN connection through an intermediary server in a remote location.
What are the protections against email spoofing?
Mitigating the risk posed by email spoofing requires a multi-layered approach to security. Security awareness training can help users to more easily spot and avoid email spoofing attempts. Email filters that use DNS authentication services like SPF, DKIM and DMARC can help to lock potentially fraudulent email.
What is an example of spoofing?
Email Spoofing For example, a scammer can assume a generic-sounding identity, like Joan Smith, and email one or several employees from the email address joan.smith@xyzwidgets.com. Joan Smith doesn't work for XYZ Widgets, a large multinational company, but the recipient works there.
What is spoofing in cyber security?
Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware. Spoofing attacks come in many forms, including: Email spoofing. Website and/or URL spoofing.
What is spoofing and how do you prevent?
Text message spoofing refers to when a scammer sends a text, but covers up their identity using an alphanumeric sender ID. The text messages usually include links to malware downloads or phishing sites. Be sure to brush up on good mobile security tips so that you don't unknowingly compromise the data on your phone.
What is anti spoofing capabilities?
Anti spoofing is the filtration of IP addresses on a network's entry point. This ingress filtration should be implemented across all networks to prevent spoofing. The technique blocks spoofed or illegitimate packets by verifying the IP address's authenticity.
What causes spoofing?
Spoofing occurs when malicious actors and cybercriminals act as trusted human contacts, brands, organizations, as well as other entities or devices so that they can access systems and infect them with malware, steal data, and otherwise cause harm and disruption.
Which software is used for spoofing?
Wireshark One of the best and widely used tools for sniffing and spoofing is Wireshark. Wireshark is a network traffic analysis tool with a plethora of capabilities. Wireshark's extensive library of protocol dissectors is one of its most distinguishing features.