What is spoofing attack in cyber security?
Spoofing is a technique through which a cybercriminal disguises themselves as a known or trusted source. Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What is meant by spoofing attack?
Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware. Spoofing attacks come in many forms, including: Email spoofing. Website and/or URL spoofing. Caller ID …
What is spoofing in cyber security?
Spoofing happens when cybercriminals use deception to appear as another person or source of information. That person can manipulate today's technology, such as email services and messages, or the underlying protocols that run the internet.
What happens during a spoofing attack?
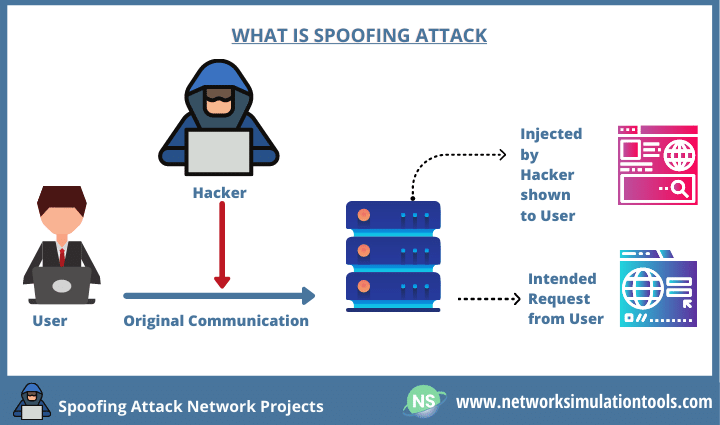
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
What is spoofing and hijacking?
DNS Spoofing is a DNS attack that changes DNS records returned to a querier;DNS Hijacking is a DNS attack that tricks the end user into thinking they are communicating with a legitimate domain name; and DNS Cache Poisoning is a DNS attack targeting caching name servers.
What is spoofing in cyber security?
Spoofing happens when cybercriminals use deception to appear as another person or source of information. That person can manipulate today's technology, such as email services and messages, or the underlying protocols that run the internet.
What happens during a spoofing attack?
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
Why is it called spoofing?
The verb and noun spoof both refer to trickery or deception, and they trace their origins back to a game called “Spoof” (or “Spouf,” depending on the source you consult), supposedly created by the British comedian and actor Arthur Roberts.
What are 4 types of spoofing attacks?
Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What is spoofing and example?
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
What is phishing vs spoofing?
Spear Phishing occurs when criminals obtain information about you from websites or social networking sites, and customize a phishing scheme to you. Spoofing describes a criminal who impersonates another individual or organization, with the intent to gather personal or business information.
Is spoofing a threat or vulnerability?
Spoofing is when an attacker impersonates an authorized device or user to steal data, spread malware, or bypass access control systems. There are many different types of spoofing, with three of the most common being: IP address spoofing – Attacker sends packets over the network from a false IP address.
What is purpose of IP spoofing?
IP address spoofing is used for two reasons in DDoS attacks: to mask botnet device locations and to stage a reflected assault. A botnet is a cluster of malware-infected devices remotely controlled by perpetrators without the knowledge of their owners.
Is spoofing Active or Passive?
Packet Spoofing is the dynamic presentation of fake network traffic that impersonates someone else. Packet Sniffing is a passive attack since attackers cannot mutilate the system in any way. In packet Spoofing, stackers inject malicious software into the victim's system.
How does spoofing happen?
Spoofing is a cybercrime that happens when someone impersonates a trusted contact or brand, pretending to be someone you trust in order to access sensitive personal information. Spoofing attacks copy and exploit the identity of your contacts, the look of well-known brands, or the addresses of trusted websites.
How can spoofing be prevented?
Packet filtering can prevent an IP spoofing attack since it is able to filter out and block packets that contain conflicting source address information. Using cryptographic network protocols such as HTTP Secure (HTTPS) and Secure Shell (SSH) can add another layer of protection to your environment.
Is spoofing and VPN the same?
Spoofing your location is just another term for faking or hiding your location. This requires changing your IP address. One of the easiest ways to spoof your location is to use a VPN. This allows you to connect to a server in another country and obtain a different IP address.
What is spoofing vs impersonation?
The main difference between impersonation and spoofing is that threat actors often register their own sending domain, instead of spoofing the target domain. This way, they pass e-mail authentication checks.
Does spoofing mean hacked?
Although spoofing can look a lot like hacking, it is actually something completely different. When your email has been spoofed, it means that someone sent an email that appeared to be from your email account but was not actually from your account.
What is spoofing and snooping?
Snooping is a form of eavesdropping with the purpose of learning information that is not intended to be visible or shared. Spoofing, on the other hand, is a method used to make an electronic device or network look like it is a trusted source.
Is spoofing and VPN the same?
Spoofing your location is just another term for faking or hiding your location. This requires changing your IP address. One of the easiest ways to spoof your location is to use a VPN. This allows you to connect to a server in another country and obtain a different IP address.
What is meant by spoofing attack?
Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware. Spoofing attacks come in many forms, including: Email spoofing. Website and/or URL spoofing. Caller ID …
What is spoofing in cyber security?
Spoofing happens when cybercriminals use deception to appear as another person or source of information. That person can manipulate today's technology, such as email services and messages, or the underlying protocols that run the internet.
What happens during a spoofing attack?
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
Does spoofing mean hacked?
Although spoofing can look a lot like hacking, it is actually something completely different. When your email has been spoofed, it means that someone sent an email that appeared to be from your email account but was not actually from your account.
What are the rules of spoofing?
Under the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value. Anyone who is illegally spoofing can face penalties of up to $10,000 for each violation.