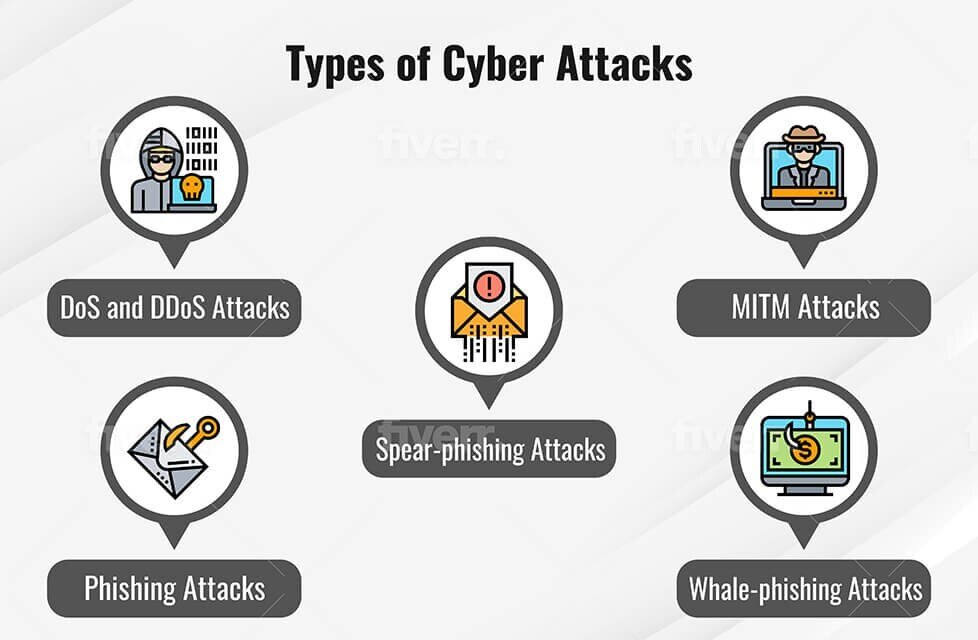
What are 3 types of attacks?
What are the four types of attacks? The different types of cyber-attacks are malware attack, password attack, phishing attack, and SQL injection attack.Types of attacks
Click-jacking
Cross-site scripting (XSS)
Cross-site request forgery (CSRF)
Man-in-the-middle (MitM)
Session hijacking
What are the top 3 types of cyber attacks?
Below are some of the most common types of cyber-attacks: Malware. Phishing. Man-in-the-middle attack (MITM)
What are the three common classes of attack?
The three common classes of attack are access, reconnaissance, and DoS.
What is attacks and its types?
There are two main types of network attacks: passive and active. In passive network attacks, malicious parties gain unauthorized access to networks, monitor, and steal private data without making any alterations. Active network attacks involve modifying, encrypting, or damaging data.
What are the top 3 types of cyber attacks?
Below are some of the most common types of cyber-attacks: Malware. Phishing. Man-in-the-middle attack (MITM)
What are the 2 basic types of attacks?
There are two types of attacks that are related to security namely passive and active attacks. In an active attack, an attacker tries to modify the content of the messages. In a passive attack, an attacker observes the messages and copies them.
What are basic attacks?
A basic attack (also called a standard, normal, or auto attack) is the default means by which a unit deals damage.
What are the four types of attacks?
Attacks can be classified into four broad categories: snooping, modification, masquerading, and denial of service. In practice, an attack may employ several of these approaches.
What are active and passive attacks?
In an active attack, System resources can be changed. While in passive attack, System resources are not changing. Active attack influences the services of the system. While in passive attack, information and messages in the system or network are acquired.
What is security attacks?
Cyber security attacks refer to the sets of actions that the threat actors perform to gain any unauthorised access, cause damage to systems/computers, steal data, or compromise the computer networks. An attacker can launch a cyber attack from any location.
What are attacks and threats?
A Threat is a possible security risk that might exploit the vulnerability of a system or asset. An attack, on the other hand, is the actual act of exploiting the information security system's weaknesses. Threats and Attacks that might jeopardize information security can be prevented in a variety of ways.
What are active attacks example?
Examples of active attacks include man-in- the middle (MitM), impersonation, and session hijacking. An attack on the authentication protocol where the attacker transmits data to the claimant, Credential Service Provider (CSP), verifier, or Relying Party (RP).
What are the top 5 cyber attacks?
The different types of cyber-attacks are malware attack, password attack, phishing attack, and SQL injection attack.
What are the top 3 most targeted industries for cyber attacks?
Keep reading to learn about data breach statistics by industry, real-life incidents that have occurred, and, of course, ways to stop malicious actors in your sphere of business. Financial, health, intellectual, and government information are the most likely to be stolen.
What are the top 3 types of cyber attacks?
Below are some of the most common types of cyber-attacks: Malware. Phishing. Man-in-the-middle attack (MITM)
What are the 3 key principles of security?
What are the 3 Principles of Information Security? The basic tenets of information security are confidentiality, integrity and availability. Every element of the information security program must be designed to implement one or more of these principles. Together they are called the CIA Triad.
What are the 3 A's in security?
Authentication, authorization, and accounting (AAA) is a term for a framework for intelligently controlling access to computer resources, enforcing policies, auditing usage, and providing the information necessary to bill for services.
What are types of threats?
Threats can be classified into four different categories; direct, indirect, veiled, conditional.
What are the 5 types of cyber attacks?
The different types of cyber-attacks are malware attack, password attack, phishing attack, and SQL injection attack.
What are three 3 physical threats to information?
Physical threat to a computer system can be as an outcome of loss of the entire computer system, damage of hardware, damage to the computer software, theft of the computer system, vandalism, natural disaster including flood, fire, war, earthquakes etc.
How many types of security attacks are there?
The most common types of DoS and DDoS attacks are the TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack, and botnets.
What are physical attacks?
Definition: An actual and intentional striking of another person against his or her will, or the intentional causing of bodily harm to an individual.
What are special attacks?
At its most basic, a Special Attack is any weapon, move, or tactic that is normally not a basic punch, kick, or whatever other form of attack the user normally uses. In fiction, especially Video Games, a Special Attack is right between a normal attack and a Limit Break.
What are blue attacks?
Light blue attacks, also known as blue attacks, do not deal damage if the protagonist's SOUL remains still. Blue attacks are the opposite of orange attacks.
What causes cyber attacks?
Cyber attacks are much more likely to occur through mundane errors like a user choosing an easy-to-guess password or not changing the default password on something like a router. ‘Phishing' is also a common way to gain access to a system, this involves extracting personal information under false pretences.
What are system based attacks?
System-based attacks It is a type of malicious software program that spread throughout the computer files without the knowledge of a user. It is a self-replicating malicious computer program that replicates by inserting copies of itself into other computer programs when executed.
What are the common types of attacks and how they work?
Understanding the common types of attacks and how they work can help inform and enhance your security strategy. As we discussed in this article, there are many different methods cybercriminals can use to infect your site, including malware, phishing, brute force, and DoS attacks. These threats require a multi-layer approach to site security.
What are the different types of malware attacks?
Several of the attack methods described above can involve forms of malware, including MITM attacks, phishing, ransomware, SQL injection, Trojan horses, drive-by attacks, and XSS attacks. In a malware attack, the software has to be installed on the target device. This requires an action on the part of the user.
What are the Big 3 types of cyber attacks?
Not all cyber attacks are created equal and in this post we hope to shed some light on the “Big 3” types of cyber attacks, malware, ransomware, and phishing attacks. We will show you examples of each attack and share with you a few tips from on how you can prepare yourself for the next major cyber attack.
What are the most common web attacks?
Attackers work within the frameworks of these kinds of requests and use them to their advantage. Some common web attacks include SQL injection and cross-site scripting (XSS), which will be discussed later in this article. Hackers also use cross-site request forgery (CSRF) attacks and parameter tampering.