Do spoof calls show up on phone bill?
Most likely it won't affect your phone bill as the call would have come from another customer's phone. No. All that would happen is that your number would show up on the receiving party's CallerID. The lack of the call in the provider records would be the proof that you didn't make the call.
Can spoof calls be detected?
While there's no completely accurate way to detect a spoofed number, there are several techniques which can help you get a fairly good idea about what's going on and may help you catch a spoofer or scammer in their tracks. Google the phone number.
What happens when a number is spoofed?
Phone spoofing occurs when fraudsters manipulate caller ID information to make it appear that they're calling from somewhere else — usually a local number or area code (known as “neighbor spoofing”) — or from government agencies like the Internal Revenue Service (IRS), Social Security Administration (SSA), or Federal …
Do calling apps show up on bill?
If you use an app, then this will send your calls via the phone's internet connection (or at least the phone company's data service) rather than the voice service, so won't show up as a phone call on the bill. It might show up as a data call, depending on exactly what the app actually does.
How do you know if someone is spoofing their number?
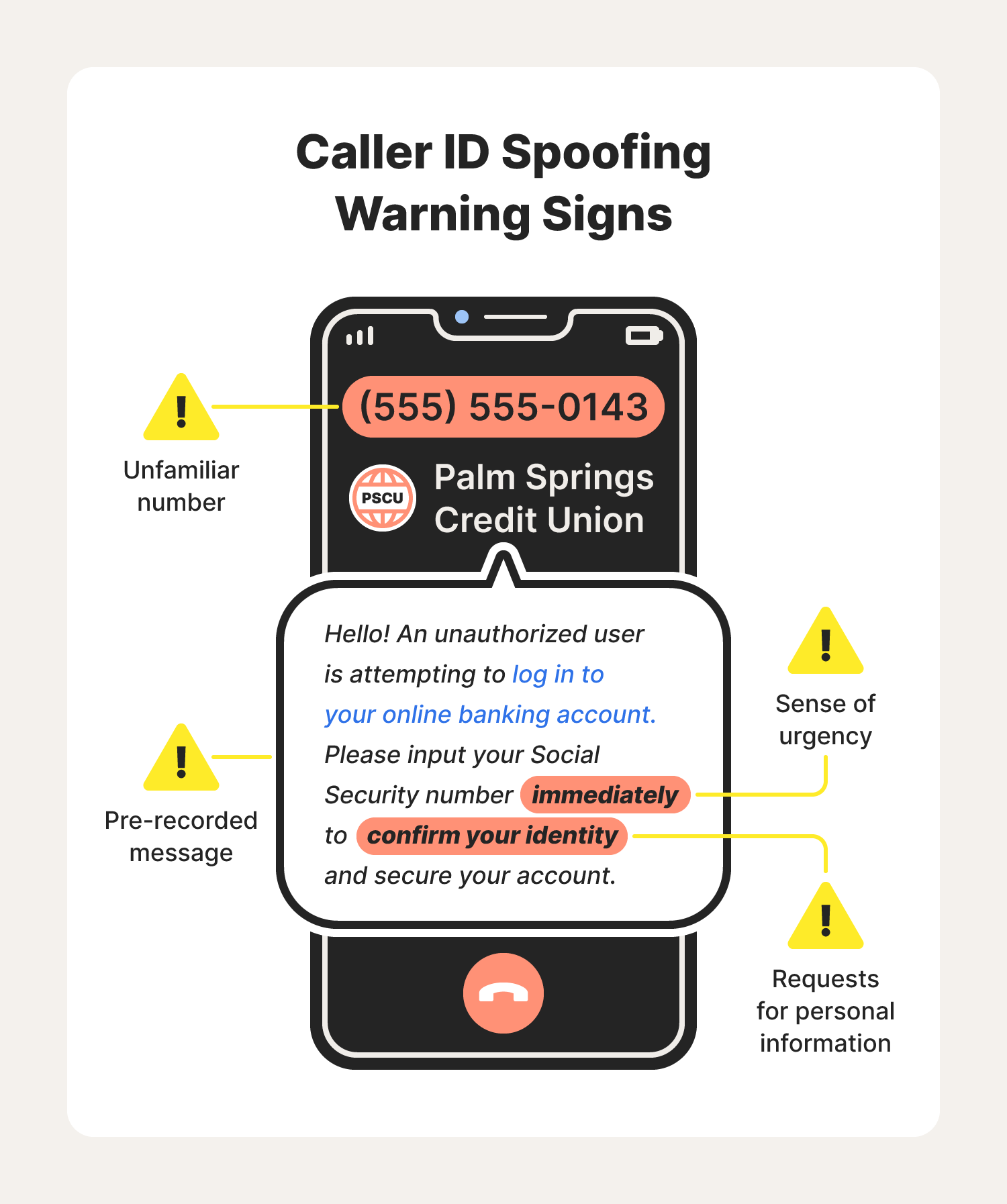
Unfamiliar number: If you recognize the caller ID display name but not the associated phone number, it may be a spoofed call. Pre-recorded messages: In some cases, caller ID spoofing may be used for robocalls. In these calls, you may be asked yes or no questions or to press a specific number for further instructions.
What happens when a number is spoofed?
Phone spoofing occurs when fraudsters manipulate caller ID information to make it appear that they're calling from somewhere else — usually a local number or area code (known as “neighbor spoofing”) — or from government agencies like the Internal Revenue Service (IRS), Social Security Administration (SSA), or Federal …
How do you know if someone is spoofing their number?
Unfamiliar number: If you recognize the caller ID display name but not the associated phone number, it may be a spoofed call. Pre-recorded messages: In some cases, caller ID spoofing may be used for robocalls. In these calls, you may be asked yes or no questions or to press a specific number for further instructions.
Is call spoofing a cyber crime?
Spoofing happens when cyber criminals take advantage of vulnerabilities in technology or its implementation. If successful, they trick people into believing that the fake email, website, phone call, text message, or other approach is genuine.
How common is number spoofing?
More often than not, you can't tell for certain that a number calling or texting you is spoofed. That said, the vast majority of phone calls coming to your phone, especially those that share your area code and exchange number, are likely to be spoofed calls.
Can I stop spoofing with my number?
Use Anti-Spoofing Applications The latest generation of call spoofing apps helps thwart call spoofing by masking your actual phone number with a secondary one. While this may sound similar to spoofers, legitimate apps hide your real phone numbers to prevent identity theft and spam.
Why is number spoofing not illegal?
However, spoofing is not always illegal. There are legitimate, legal uses for spoofing, like when a doctor calls a patient from her personal mobile phone and displays the office number rather than the personal phone number or a business displays its toll-free call-back number. What is blocking or labeling?
What calls show up on phone bill?
For some plans, your phone bill may show the incoming number and that the inbound call is being forwarded. For other plans that don't display forwarded calls, you might not see the calls on your phone bill since all inbound calls are being forwarded to a Firewall number.
What shows up on your phone bill?
Voice usage and call details, includes phone numbers dialed and received, call length, and call time. Messaging usage details, includes the phone numbers and time of messages sent and received for text, picture, and video messages. Data usage details, includes download size and data usage time.
What shows up as data on phone bill?
Cell phone bills used to only contain charges related to the number of minutes spent on phone calls. With smartphones and instant access to the Internet, today's monthly bills are mostly about how much data you're using. Every time you use the Internet to do something on your phone, your monthly data meter goes up.
Can someone trace your calls?
Long story short: yes, someone can monitor your phone to keep tabs on all your activities. This includes phone calls, texts, browser activity, photos, videos, apps, and more. This is often done via spyware, a form of malware designed for monitoring a device's activity remotely.
Can your location be tracked through a call?
Unfortunately, yes. From finding your physical location to uncovering personal information, anyone with access to your phone number is able to stalk you and discover your exact location. It's also very hard to determine whether or not your phone is being tracked or monitored.
Can hackers track your phone calls?
If your phone has been bugged or tapped, any activities you do on your phone could be recorded and transferred to a third party. Private data, including your GPS location, text messages, phone calls, and more could be at risk for being exposed.
What happens when a number is spoofed?
Phone spoofing occurs when fraudsters manipulate caller ID information to make it appear that they're calling from somewhere else — usually a local number or area code (known as “neighbor spoofing”) — or from government agencies like the Internal Revenue Service (IRS), Social Security Administration (SSA), or Federal …
Is VPN a spoofing?
A VPN is one of the tools you can use to change, hide or spoof your online location. VPNs can mask your IP address, changing them to an IP address in the location of your choosing. However, this will not be enough for some websites and apps which also check for GPS locations and DNS leaks too.
Is spoofing serious?
A successful spoofing attack can have serious consequences – including stealing personal or company information, harvesting credentials for use in further attacks, spreading malware, gaining unauthorized network access, or bypassing access controls.
Is spoofing risky?
Spoofing poses a significant risk to individuals and businesses as it can lead to financial crimes such as money laundering, identity theft, and fraud.
Is spoofing SMS illegal?
SMS spoofing is legal when used for legitimate purposes, like when an organization or agency uses their real name as the sender ID instead of the seemingly random number that their communication was actually sent from. However, sending a spoof text message is illegal if used for malicious purposes or to commit fraud.
Can someone track your phone by texting you?
Yes, it is possible to track a location through text messages using specific tracking tools and techniques. Some tracking apps and services can send silent text messages to a target device, prompting it to share its location data.
Can hackers find your location through text?
In Short. Researchers have warned about a new SMS vulnerability that could enable hackers to track users' locations. The vulnerability lies in the automated delivery notification feature of SMS. As of now, the vulnerability has been observed mainly in Android operating systems.
Why do I get so many spoofed calls?
Getting a lot of unwanted calls would mean your number has been sold to a scammer group. Once your number is sold, it's used by all the scammers who have access to it. They try to defraud you in multiple ways by posing as professionals. Some might pretend to be from insurance agencies.
What is the most common type of spoofing?
One of the most common types of spoofing attacks is email spoofing. This occurs when an attacker purports to be a known, familiar or plausible contact by either altering the “From” field to match a trusted contact or mimicking the name and email address of a known contact.