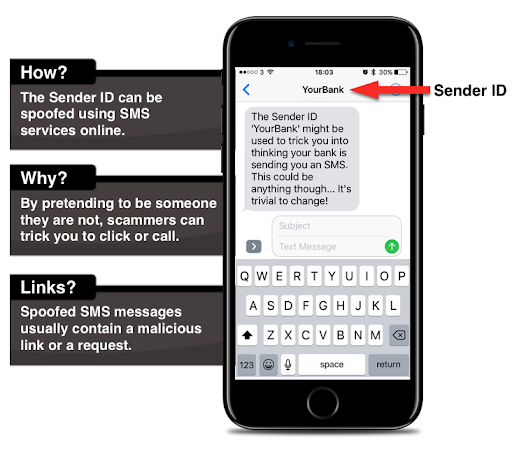
Does spoofing work on text messages?
Yes, someone can send spoof text messages using your number. Scammers usually do this when they want to text their targets from a local number. A scammer could also target someone you know and try to trick them by spoofing your phone number.
Can spoofing occur through text messages?
SMS spoofing is sometimes referred to as SMS phishing. Both terms relate to the fraudulent practice of purporting to be from a legitimate source to get individuals to reveal personal information. Phishing can occur through emails (the most common method), phone calls, and text messages.
Can SMS short codes be spoofed?
SMS short codes also cannot be easily spoofed – where a con man disguises his number so that it shows up on your caller ID looking like it really is the IRS, a utility, or some other organization calling.
Does spoofing really work?
So, yes: you can put any number into a spoofer, and the person receiving the call might assume (from the number) the call is from someone they know. But there are certain phone numbers which are obviously spoofed.
Can you go to jail for spoofing?
The former head of JPMorgan Chase & Co.'s precious-metals desk and his top trader were sentenced to prison for spoofing, fraud and attempted market manipulation.
How illegal is spoofing?
When is spoofing illegal? Under the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value. Anyone who is illegally spoofing can face penalties of up to $10,000 for each violation.
Can SMS be sent anonymously?
Android phones Tap Additional Settings, then Caller ID. Open the Caller ID drop-down menu and select Hide My Number.
Can malware be sent via SMS?
SMS Attacks and Mobile Malware Threats SMS attacks, in particular, pose a significant threat to all mobile users. SMS attacks involve the creation and distribution of malware by cybercriminals designed to target a victim's mobile device.
Can iMessage be spoofed?
Apple takes security very seriously. When using iMessage instead of SMS, addresses are verified which protects against these kinds of spoofing attacks.
Can phone numbers be spoofed?
Practically any number can be spoofed, meaning scammers can target any phone number they have in their database. Many scammers don't stop at just spoofing caller ID numbers. Some will use digital tech tools to change the display name on the caller ID, as well.
Are SMS texts private?
Standard SMS is not and will never be end-to-end encrypted. SMS encryption is performed wholly by mobile carriers who typically use weak encryption such as CDMA or GSM. SMS messages are sent in plain text, meaning anyone snooping on traffic can intercept and read them.
How did someone get a text from me that I didn't send?
This is termed SMS spoofing. It's when an attacker leverages a PBX (Private Branch Exchange) to trick a targeted device into believing it's receiving a message from another source. To achieve this the attacker must either obtain a PBX licence themselves, or obtain access to an app or software with an API for a PBX.
Is spoofing hard to detect?
Spoofing of a caller ID is difficult to detect without answering the phone call, because the phone number may look legitimate. However, there are some telltale signs of caller ID spoofing once you answer, according to the Federal Communications Commission (FCC).
Is spoofing a crime?
When is spoofing illegal? Under the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value. Anyone who is illegally spoofing can face penalties of up to $10,000 for each violation.
Is spoofing risky?
Spoofing poses a significant risk to individuals and businesses as it can lead to financial crimes such as money laundering, identity theft, and fraud.
Can a text message be malicious?
SMS attacks definition SMS attacks are malicious threats that use short message service (SMS) and other mobile-based messaging applications to engage in cyberattacks. These attacks utilize malicious software and websites to enact damage to users.
What can spoofing occur through?
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
Is there a way to tell if your phone has been spoofed?
There are a number of telltale signs which indicate that your number is being spoofed. If your spoofed phone number is being used to spam lots of potential victims, you may notice: Incoming calls or text messages responding to communications you didn't initiate. Calls or messages from people asking who you are.
Can texts contain malware?
Can I get a virus from opening a text? The likelihood of you receiving a virus from opening a text is low. It usually takes clicking on an infected link or file to trigger a virus to install onto a device.
Can spoofing occur through text messages?
SMS spoofing is sometimes referred to as SMS phishing. Both terms relate to the fraudulent practice of purporting to be from a legitimate source to get individuals to reveal personal information. Phishing can occur through emails (the most common method), phone calls, and text messages.
Is spoofing traceable?
It may be possible to track down a spoofer by convincing a phone carrier and law enforcement to begin an investigation but this can be incredibly time consuming and still isn't guaranteed to get the result you require.
Is spoofing a hack?
The key difference between spoofing and hacking comes down to this: “If your device is compromised, that would be considered your device has been hacked — if it's your identity that has been compromised, you've been spoofed or impersonated,” said Kulm.
Will spoofing get me banned?
While spoofing is against the terms of service of Pokémon Go and can result in a ban, some players may still be tempted to try it.
Is spoofing a VPN?
A VPN is the most common type of IP spoofing. Although it's not technically an attack, it employs the same principles. A VPN will hide your real IP address so you can move around the internet without anyone knowing where you're located.
What WTF is spoofing?
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
What is a real example for spoofing?
For example, a scammer can assume a generic-sounding identity, like Joan Smith, and email one or several employees from the email address [email protected]. Joan Smith doesn't work for XYZ Widgets, a large multinational company, but the recipient works there.