What are the common types of attacks and how they work?
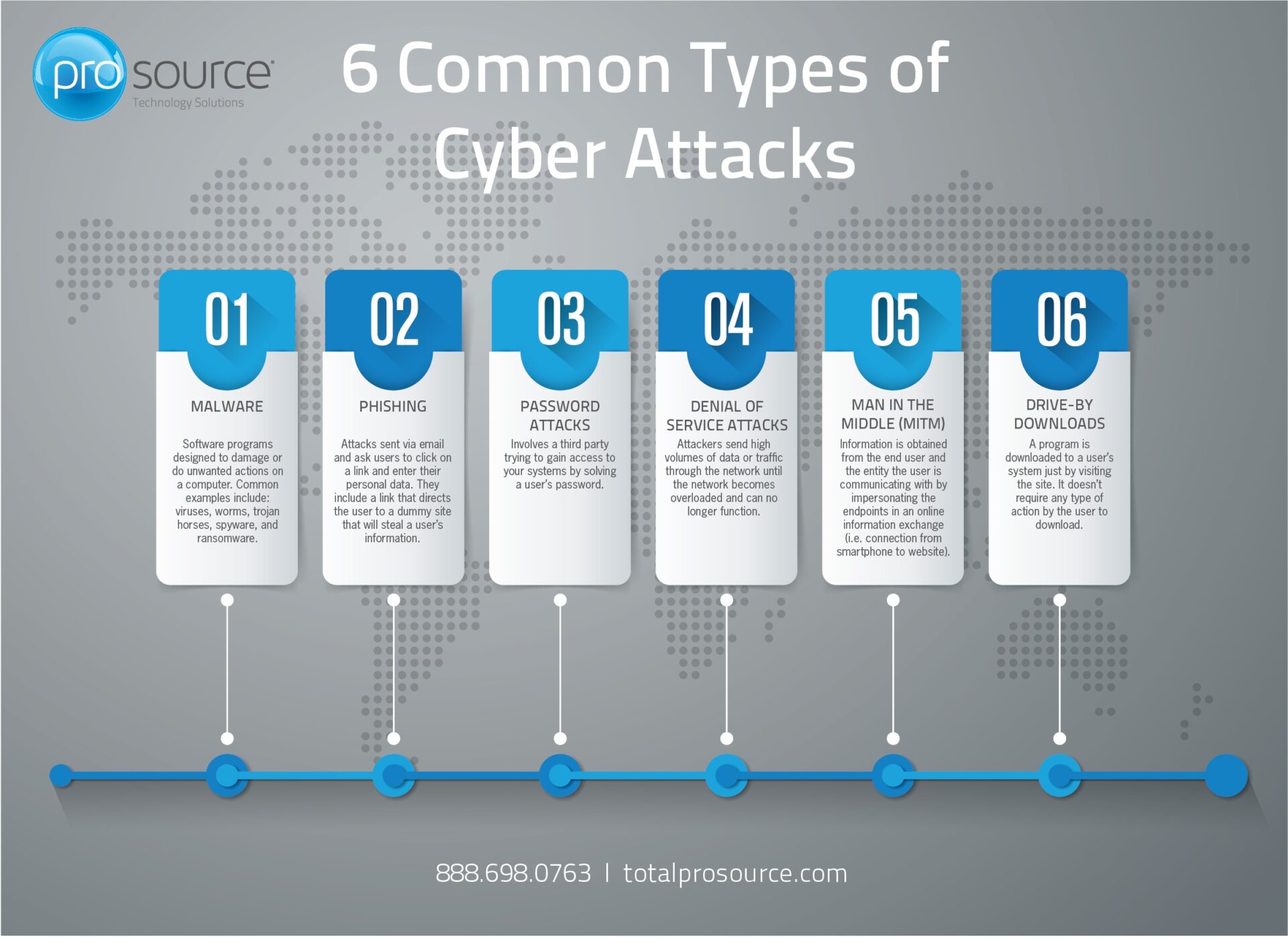
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
What is the most common attack type?
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
What is the most common attack type?
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
What are basic attacks?
A basic attack (also called a standard, normal, or auto attack) is the default means by which a unit deals damage.
How do cyber attacks work?
How are cyber attacks carried out? Many cyber attacks are opportunistic, with hackers spotting vulnerabilities in a computer system's defences and exploiting them. This may involve finding flaws in the code of a website, that allows them to insert their own code and then bypass security or authentication processes.
What are the 3 major types of cyber security?
The 3 major types of cyber security are network security, cloud security, and physical security. Your operating systems and network architecture make up your network security. It can include network protocols, firewalls, wireless access points, hosts, and servers.
What are the security attacks?
An attempt to gain unauthorized access to information resource or services, or to cause harm or damage to information systems.
What are the four main purposes of an attack?
Explanation: The four main purposes of an attack are denial of availability, data modification, data export, and as a launch point. What tool might be used by an attacker during the reconnaissance phase of an attack to glean information about domain registrations?
What is an example of an active attack?
An attack on the authentication protocol where the attacker transmits data to the claimant, Credential Service Provider (CSP), verifier, or Relying Party (RP). Examples of active attacks include man-in-the-middle (MitM), impersonation, and session hijacking.
What are the three common classes of attack?
As stated, the three types of attacks are reconnaissance, access, and DoS. Reconnaissance is both a type of attack and a phase of an attack. Intruders typically perform reconnaissance on a target network before attempting to access or disrupt the network resources.
Is phishing the most common cyber attack?
Phishing is the most common form of cyber crime, with an estimated 3.4 billion spam emails sent every day. The use of stolen credentials is the most common cause of data breaches. Google blocks around 100 million phishing emails daily.
What is the most common attack type?
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
What are the 4 attacks on computer system security?
Malware or Malicious software is the term that encompasses various types of attacks including spyware, viruses, and worms. Malware uses a vulnerability to breach a network when a user clicks a “planted” dangerous link or email attachment, which is used to install malicious software inside the system.
What are the four categories of attacks and explain one of them?
Attacks can be classified into four broad categories: snooping, modification, masquerading, and denial of service. In practice, an attack may employ several of these approaches.
How many attacks are there in cyber security?
How Many Cyber Attacks Happen Per Day In The World? Nearly 4000 new cyber attacks occur every day. Every 14 seconds, a company falls victim to a ransomware attack, which can result in devastating financial losses while 560,000 new pieces of malware are detected every day.
What is active and passive attack?
In an Active attack, an attacker tries to modify the content of the messages. On the other hand, in a Passive attack, an attacker observes the messages, copy them and may use them for malicious purposes. Read this article to find out more about Active and Passive attacks and how they are different from each other.
What are the two types of attacks in the army?
Fire attacks – reconnaissance by fire is used by apprehensive soldiers when they suspect the enemy is nearby. Force concentration – the practice of concentrating a military force against a portion of an enemy force.
What are basic attacks in injustice?
Basic attacks are the most universally used attacks and are available to every single character at any level. They are performed by tapping (light) or swiping (heavy) the screen. Light basic attacks are faster, but heavy basic attacks do more damage.
What is active attacks in security?
Active attacks are attacks in which the hacker attempts to change or transform the content of messages or information. These attacks are a threat to the integrity and availability of the system. Due to these attacks, systems get damaged, and information can be altered.
Who do DDOS attacks target?
The target can be a server, website or other network resource. The flood of incoming messages, connection requests or malformed packets to the target system forces it to slow down or even crash and shut down, thereby denying service to legitimate users or systems.
What are the different types of attacks on transport layer?
The attacks of the transport layer are: TCP sequence prediction, UDP &TCP flooding. During this study it was observed that are many other attacks that effectes physical layer such as eavesdropping, jamming and network injection.
What is the meaning of DDoS?
DDoS attack means “Distributed Denial-of-Service (DDoS) attack” and it is a cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites.
What are the four types of threats?
Threats can be classified into four different categories; direct, indirect, veiled, conditional. A direct threat identifies a specific target and is delivered in a straightforward, clear, and explicit manner.
What is the most common security threat?
Malware has become one of the most significant external threat to systems. Malware can cause widespread damage and disruption, and requires huge efforts within most organizations. Spyware, a malware intended to violate privacy, has also become a major concern to organizations.
What is the most popular security threat?
1) Phishing Attacks The biggest, most damaging and most widespread threat facing small businesses is phishing attacks. Phishing accounts for 90% of all breaches that organizations face, they've grown 65% over the last year, and they account for over $12 billion in business losses.
What are targeted attacks?
A targeted attack refers to a type of threat in which threat actors actively pursue and compromise a target entity's infrastructure while maintaining anonymity. These attackers have a certain level of expertise and have sufficient resources to conduct their schemes over a long-term period.