What does spoofing mean in cyber security?
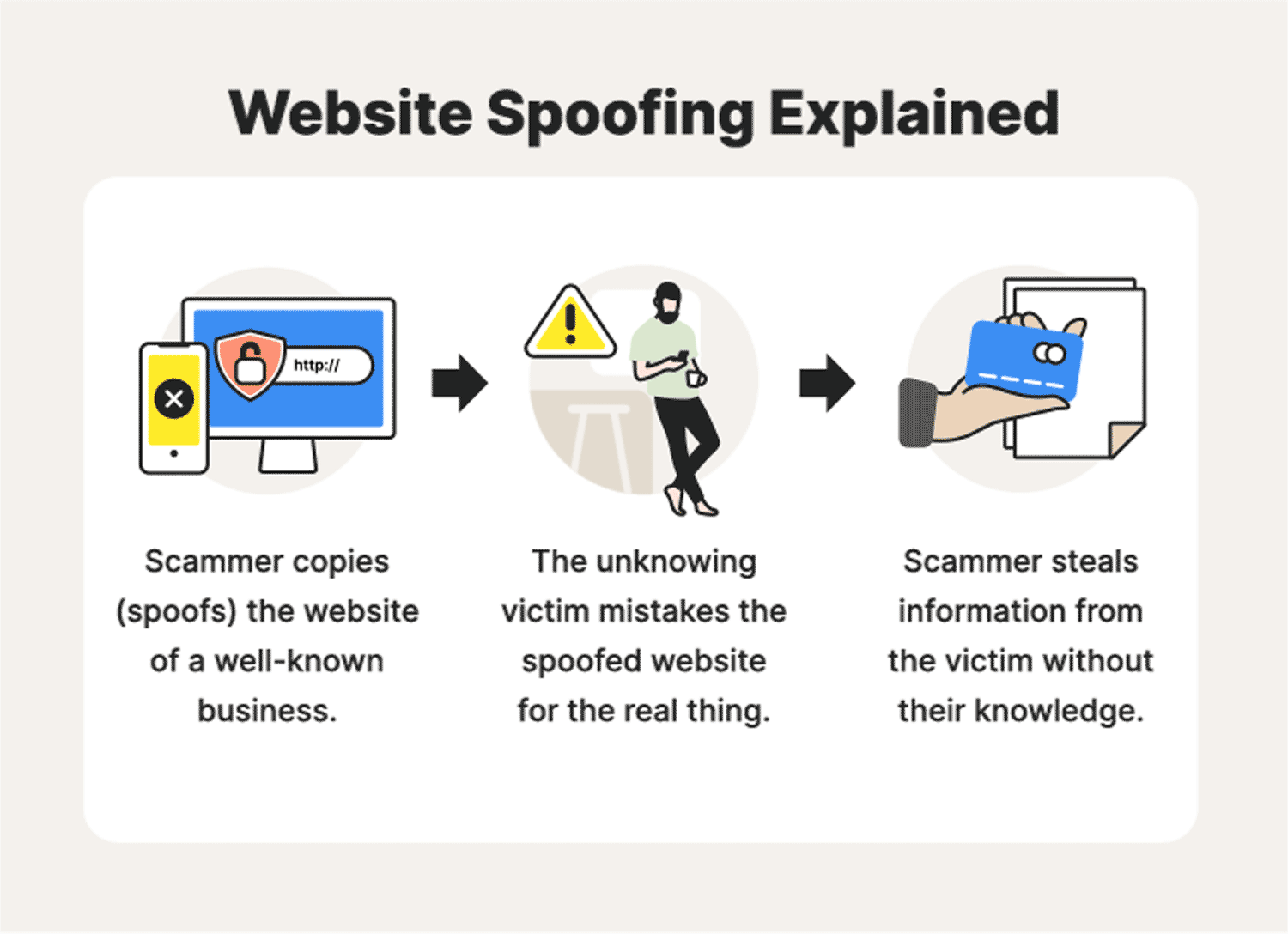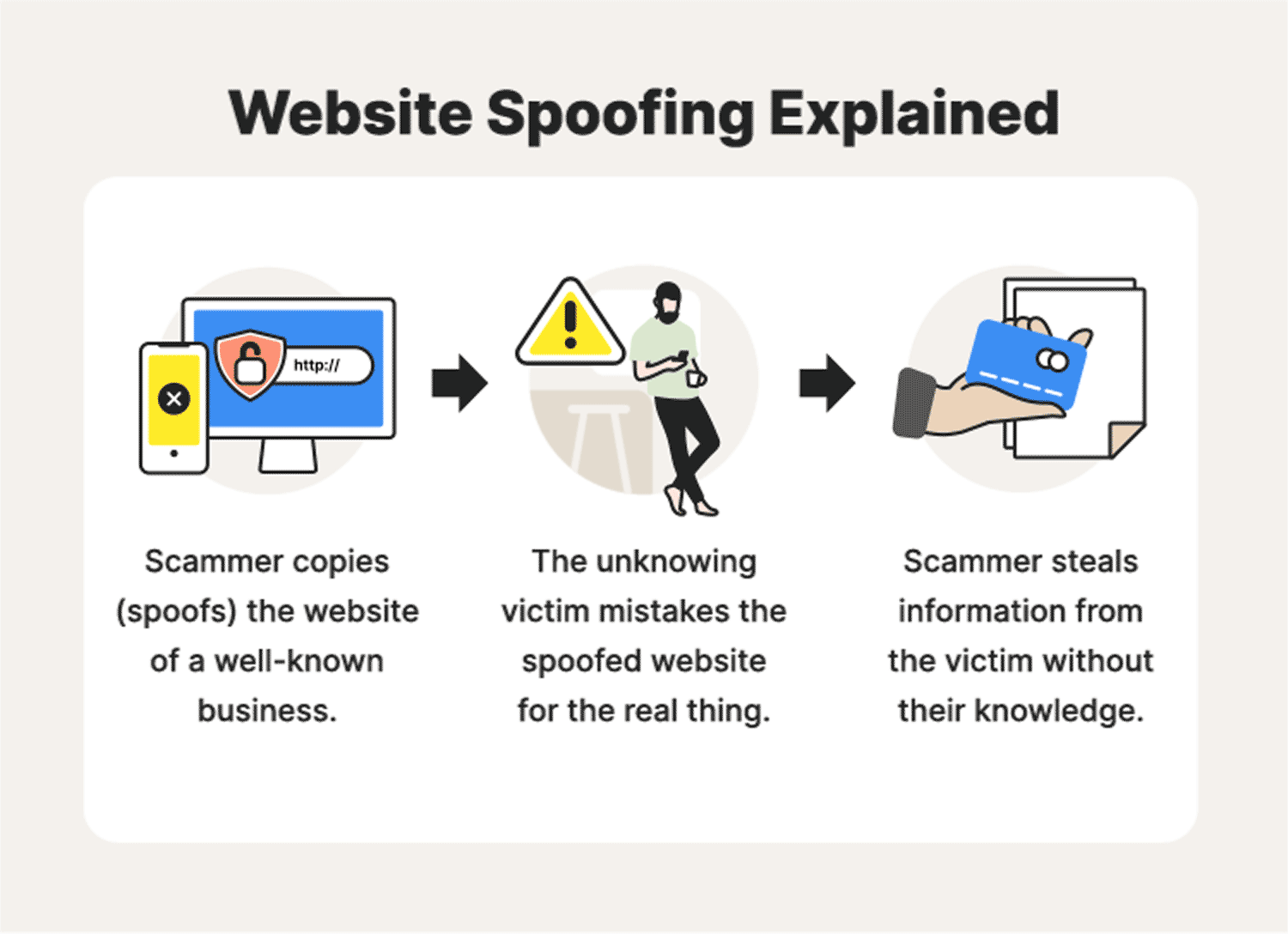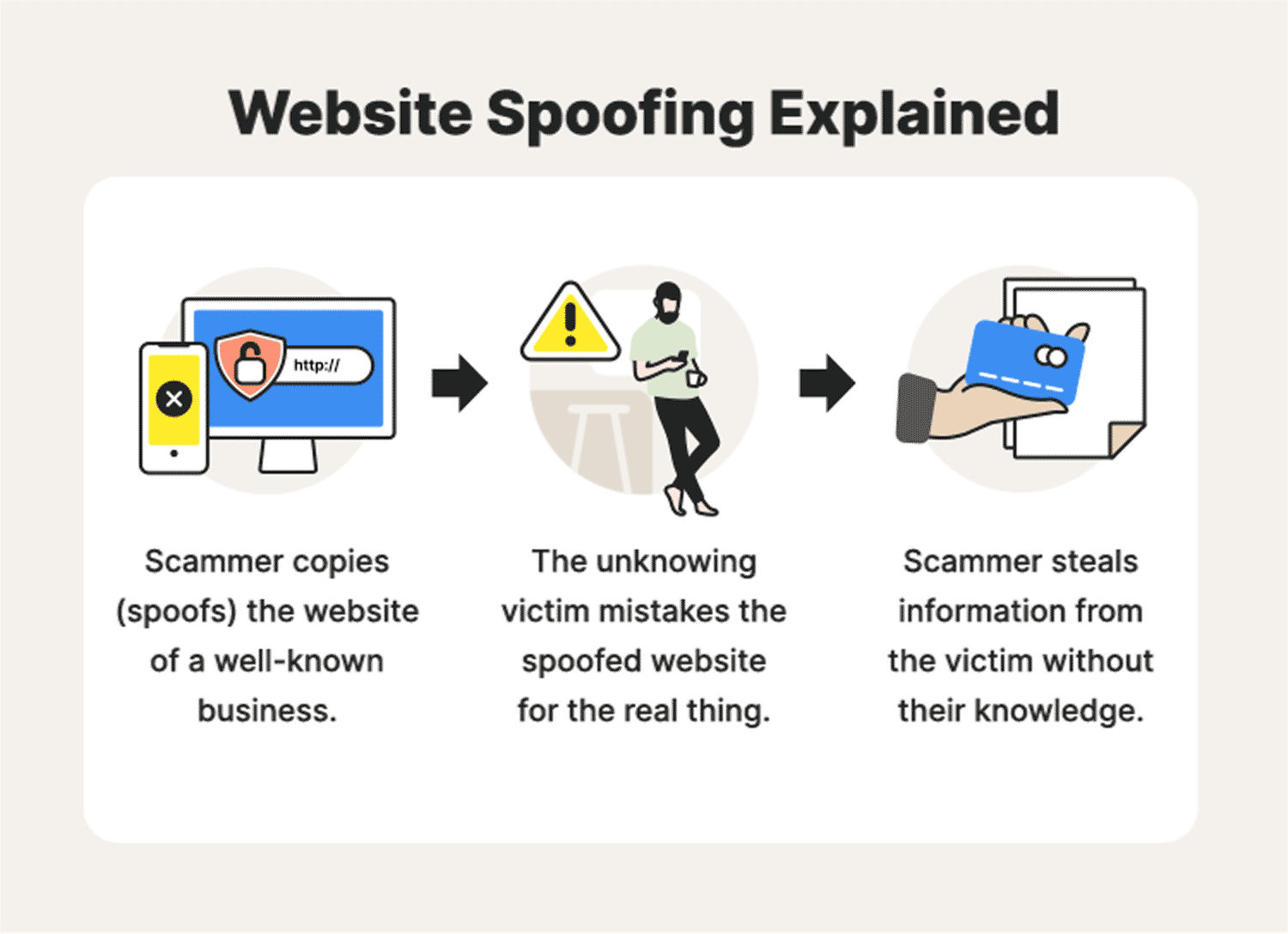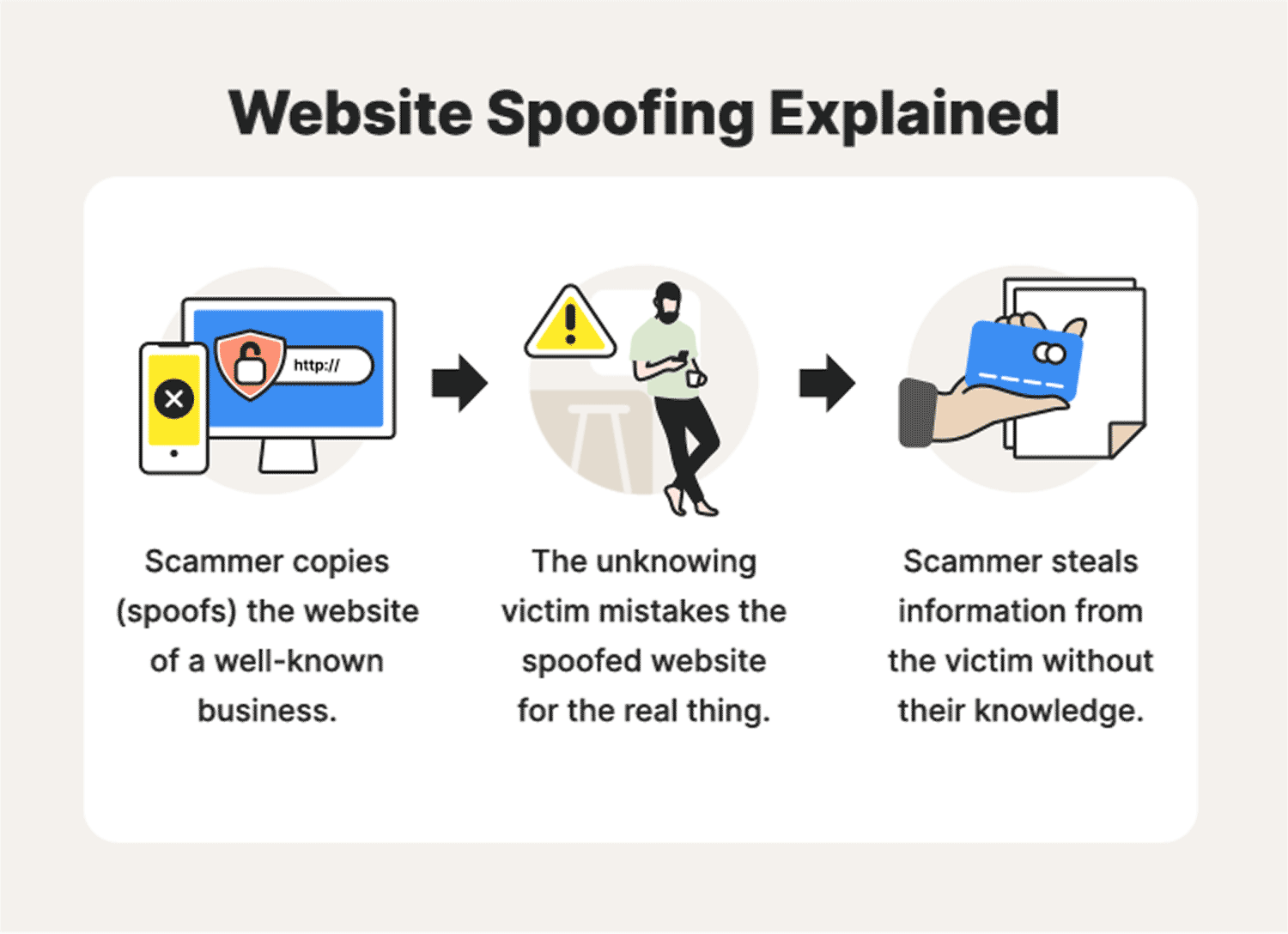
Spoofing is a technique through which a cybercriminal disguises themselves as a known or trusted source. Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What is spoofing in simple words?
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
Is spoofing an attack?
Spoofing is the act of disguising a communication or identity so that it appears to be associated with a trusted, authorized source. Spoofing attacks can take many forms, from the common email spoofing attacks that are deployed in phishing campaigns to caller ID spoofing attacks that are often used to commit fraud.
What is spoofing vs phishing?
Spoofing is a technique used to disguise the sender's identity, while phishing is a method used to trick the recipient into divulging personal information or performing an action.
What is spoofing in simple words?
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
What is a real example for spoofing?
For example, a scammer can assume a generic-sounding identity, like Joan Smith, and email one or several employees from the email address joan.smith@xyzwidgets.com. Joan Smith doesn't work for XYZ Widgets, a large multinational company, but the recipient works there.
How do hackers use spoofing?
Email spoofing is a type of cyberattack that targets businesses by using emails with forged sender addresses. Because the recipient trusts the alleged sender, they are more likely to open the email and interact with its contents, such as a malicious link or attachment.
What happens if you get spoofed?
If you're one of the unlucky victims whose number is chosen by phone spoofing scammers, it can lead to damaging and scary consequences, such as: An overwhelming amount of angry phone calls and messages from targets or victims. A massive phone bill if scammers use a SIM swapping scam to take over your phone number.
Is VPN a spoofing?
A VPN is the most common type of IP spoofing. Although it's not technically an attack, it employs the same principles. A VPN will hide your real IP address so you can move around the internet without anyone knowing where you're located.
What is the most common spoofing attack?
The most common spoofing attacks are IP address attacks, email phishing attacks, and website domain attacks. They vary in volume, frequency, and method. IP spoofing attacks like DDoS or Man-in-the-Middle are high volume and attack tech vulnerabilities. Domain spoofing attacks are low volume and attack human nature.
Is spoofing a malware?
Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware. Spoofing attacks come in many forms, including: Email spoofing.
Why is spoofing illegal?
When is spoofing illegal? Under the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value. Anyone who is illegally spoofing can face penalties of up to $10,000 for each violation.
Can a phone number be spoofed?
Phone number spoofing causes the Caller ID to display a phone number or other information to make it look like the calls are from a different person or business. While the caller's information may appear local, the calls are often placed by telemarketers located outside the state or country.
Why is it called spoofing?
The verb and noun spoof both refer to trickery or deception, and they trace their origins back to a game called “Spoof” (or “Spouf,” depending on the source you consult), supposedly created by the British comedian and actor Arthur Roberts.
What is spoofing and why is it illegal?
When is spoofing illegal? Under the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value. Anyone who is illegally spoofing can face penalties of up to $10,000 for each violation.
What happens if you get spoofed?
If you're one of the unlucky victims whose number is chosen by phone spoofing scammers, it can lead to damaging and scary consequences, such as: An overwhelming amount of angry phone calls and messages from targets or victims. A massive phone bill if scammers use a SIM swapping scam to take over your phone number.
What is an example of email spoofing?
As an example of email spoofing, an attacker might create an email that looks like it comes from PayPal. The message tells the user that their account will be suspended if they don't click a link, authenticate into the site, and change the account's password.
What is spoofing in simple words?
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
Why do people get spoofed?
In cybersecurity, ‘spoofing' is when fraudsters pretend to be someone or something else to win a person's trust. The motivation is usually to gain access to systems, steal data, steal money, or spread malware.
Why do people do spoofing?
Spoofing criminals try to gain your trust, and they count on making you believe that the spoofed communications are legitimate. Often, using the name of a big, trusted company—such as Amazon or PayPal—is enough to get targets to take some kind of action or reveal information.
Who uses spoofing?
Cybercriminals use spoofing to trick victims into revealing personal information by posing as a trusted brand or contact. Websites and emails are most commonly spoofed online. But attackers use other means as well, including caller ID spoofing, IP spoofing, and “Man-in-the-Middle” attacks.
Does VPN prevent spoofing?
DNS Spoofing (DNS Poisoning) VPNs can keep you safe from DNS poisoning by encrypting your DNS requests and good providers like ExpressVPN and NordVPN even handle them through their own DNS servers (read our ExpressVPN review).
Does spoofing change your IP?
Internet Protocol (IP) spoofing is a type of malicious attack where the threat actor hides the true source of IP packets to make it difficult to know where they came from. The attacker creates packets, changing the source IP address to impersonate a different computer system, disguise the sender's identity or both.
How can we protect against spoofing?
To prevent spoofing attacks, you can restrict traffic to only recognized IP addresses, trusted MAC addresses, and IP-MAC pairs. You can also set traffic limits and flags to prevent DoS attacks and create rules to bypass DoS inspection. The firewall logs dropped traffic.
How do spammers get my phone number?
They accumulate your data through sources like warranty cards, online purchases, even searching for number online to build a more lucrative file to sell. Here are a few examples: “800”, “888”, and “900” numbers are another way for telemarketers to obtain your phone number.
Can you stop email spoofing?
As an ordinary user, you can stop email spoofing by choosing a secure email provider and practicing good cybersecurity hygiene: Use throwaway accounts when registering in sites. That way, your private email address won't appear in shady lists used for sending spoofed email messages in bulk.