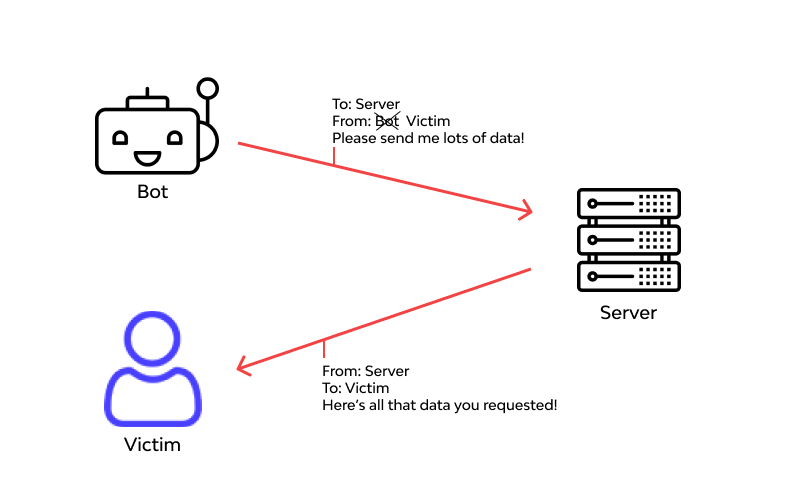
What kind of attack is an example of IP spoofing?
What are examples of IP spoofing? When attackers launch a DDoS attack, they use spoofed IP addresses to overwhelm computer servers with packet volumes too large for the destination computers to handle. Botnets are often used to send geographically dispersed packets.
What type of attack is spoofing?
Spoofing is a technique through which a cybercriminal disguises themselves as a known or trusted source. Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What is an IP spoofing attack?
IP address spoofing is the act of falsifying the content in the Source IP header, usually with randomized numbers, either to mask the sender's identity or to launch a reflected DDoS attack, as described below.
What kind of attack is an example of IP spoofing quizlet?
What is IP Spoofing? IP Address spoofing – process of creating IP packets with forged source IP address to impersonate legitimate system. This kind of spoofing is often used in DoS attacks (Smurf Attack).
Is IP spoofing a passive attack?
Packet Spoofing is the dynamic presentation of fake network traffic that impersonates someone else. Packet Sniffing is a passive attack since attackers cannot mutilate the system in any way. In packet Spoofing, stackers inject malicious software into the victim's system.
What is an IP spoofing attack?
IP address spoofing is the act of falsifying the content in the Source IP header, usually with randomized numbers, either to mask the sender's identity or to launch a reflected DDoS attack, as described below.
Is spoofing an active attack?
Spoofing is often the way a bad actor gains access in order to execute a larger cyber attack such as an advanced persistent threat or a man-in-the-middle attack.
What are 3 types of attacks?
What are the four types of attacks? The different types of cyber-attacks are malware attack, password attack, phishing attack, and SQL injection attack.
Is spoofing a malware attack?
Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware. Spoofing attacks come in many forms, including: Email spoofing. Website and/or URL spoofing.
What happens in spoof attack?
In a website spoofing attack, a scammer will attempt to make a malicious website look exactly like a legitimate one that the victim knows and trusts. Website spoofing is often associated with phishing attacks.
Is ping broadcast a DoS attack?
Ping flood, also known as ICMP flood, is a common Denial of Service (DoS) attack in which an attacker takes down a victim's computer by overwhelming it with ICMP echo requests, also known as pings.
What kind of attack is an example of IP spoofing ARP poisoning?
Address Resolution Protocol (ARP) spoofing or ARP poisoning is a form of spoofing attack that hackers use to intercept data. A hacker commits an ARP spoofing attack by tricking one device into sending messages to the hacker instead of the intended recipient.
Which of the following is an example of spoofing?
In its most primitive form, spoofing refers to impersonation via telephone. For example, when a caller on the other end falsely introduces themselves as a representative of your bank and asks for your account or credit card info, you are a victim of phone spoofing.
Is spoofing a threat or vulnerability?
Spoofing is when an attacker impersonates an authorized device or user to steal data, spread malware, or bypass access control systems. There are many different types of spoofing, with three of the most common being: IP address spoofing – Attacker sends packets over the network from a false IP address.
Which attack is passive attack?
A passive attack is a network attack in which a system is monitored and sometimes scanned for open ports and vulnerabilities. The purpose of a passive attack is to gain information about the system being targeted; it does not involve any direct action on the target.
Which is the type of passive attack?
An eavesdropping attack is considered a type of passive attack. The goal of an eavesdropping assault is to steal data sent between two devices connected to the internet. Eavesdropping includes traffic analysis.
What is passive and active attack?
Definition. In active attacks, the attacker intercepts the connection and efforts to modify the message's content. In passive attacks, the attacker observes the messages, then copy and save them and can use it for malicious purposes.
Is spoofing a threat or vulnerability?
Spoofing is when an attacker impersonates an authorized device or user to steal data, spread malware, or bypass access control systems. There are many different types of spoofing, with three of the most common being: IP address spoofing – Attacker sends packets over the network from a false IP address.
Is spoofing a type of phishing?
Phishing schemes often use spoofing techniques to lure you in and get you to take the bait. These scams are designed to trick you into giving information to criminals that they shouldn't have access to.
What is an IP spoofing attack?
IP address spoofing is the act of falsifying the content in the Source IP header, usually with randomized numbers, either to mask the sender's identity or to launch a reflected DDoS attack, as described below.
What are the examples of active attack?
Examples of active attacks include man-in- the middle (MitM), impersonation, and session hijacking. An attack on the authentication protocol where the attacker transmits data to the claimant, Credential Service Provider (CSP), verifier, or Relying Party (RP).
Which are active attacks?
An active attack is a network exploit in which a hacker attempts to make changes to data on the target or data en route to the target. There are several different types of active attacks. However, in all cases, the threat actor takes some sort of action on the data in the system or the devices the data resides on.
What are the 2 basic types of attacks?
There are two types of attacks that are related to security namely passive and active attacks. In an active attack, an attacker tries to modify the content of the messages. In a passive attack, an attacker observes the messages and copies them.
Is spoofing phishing?
Phishing schemes often use spoofing techniques to lure you in and get you to take the bait. These scams are designed to trick you into giving information to criminals that they shouldn't have access to.
What is a malware attack?
Malware is software that is installed on a computer without the user's consent and that performs malicious actions, such as stealing passwords or money. There are many ways to detect malware, but the most common is to scan the computer for malicious files or programs.
How is IP spoofing possible?
Internet Protocol (IP) spoofing is a type of malicious attack where the threat actor hides the true source of IP packets to make it difficult to know where they came from. The attacker creates packets, changing the source IP address to impersonate a different computer system, disguise the sender's identity or both.