Which spoofing is one of the very commonly used phishing technique?
Website Spoofing Methods As mentioned above, URL cloaking is a popular method. Through the use of specialized scripts, phishers can cover up the true URL with one that is associated with a trusted website. Subdomains are also commonly used to confuse Internet users and to lend them false senses of security.
What is the most common used method for phishing?
1. Email phishing. Most phishing attacks are sent by email. The crook will register a fake domain that mimics a genuine organisation and sends thousands of generic requests.
What is the most common spoofing?
One of the most common types of spoofing attacks is email spoofing. This occurs when an attacker purports to be a known, familiar or plausible contact by either altering the “From” field to match a trusted contact or mimicking the name and email address of a known contact.
What are the most common spoofing attacks?
Spoofing attacks may deploy malware in your system, direct users to a fake phishing page, and steal user data. The most common spoofing attacks are IP address attacks, email phishing attacks, and website domain attacks. They vary in volume, frequency, and method.
What is spoofing in phishing?
Differences Between Spoofing and Phishing Purpose: The goal of spoofing is to impersonate someone's identity while the purpose of phishing attacks is to steal information. Nature: Spoofing is not considered fraud because the victim's email address or phone number are not stolen but rather imitated.
What is the most common used method for phishing?
1. Email phishing. Most phishing attacks are sent by email. The crook will register a fake domain that mimics a genuine organisation and sends thousands of generic requests.
What is a common example of phishing?
An email from PayPal arrives telling the victim that their account has been compromised and will be deactivated unless they confirm their credit card details. The link in the phishing email takes the victim to a fake PayPal website, and the stolen credit card information is used to commit further crimes.
How common is spoofing?
Email spoofing is the most popular method, with a staggering 3.1 billion spoofed emails sent every day, according to email security firm Proofpoint.
How common are spoofing attacks?
What are name spoofing attacks?
Display name spoofing is when a hacker creates an email account using a first and last name (display name) that will appear familiar to the recipient. Email attacks like CEO Fraud, Spear-Phishing and Whaling utilize this tactic and it is especially effective when email is viewed on mobile devices.
What is spoofing example in cyber security?
Fake job offers, fake banking-related messages, fake lottery messages, money refund scams, and password reset messages are some examples of Text Message Spoofing. Spoofed messages are difficult to identify until the person is aware of where to look for them.
What is an example of email spoofing?
As an example of email spoofing, an attacker might create an email that looks like it comes from PayPal. The message tells the user that their account will be suspended if they don't click a link, authenticate into the site, and change the account's password.
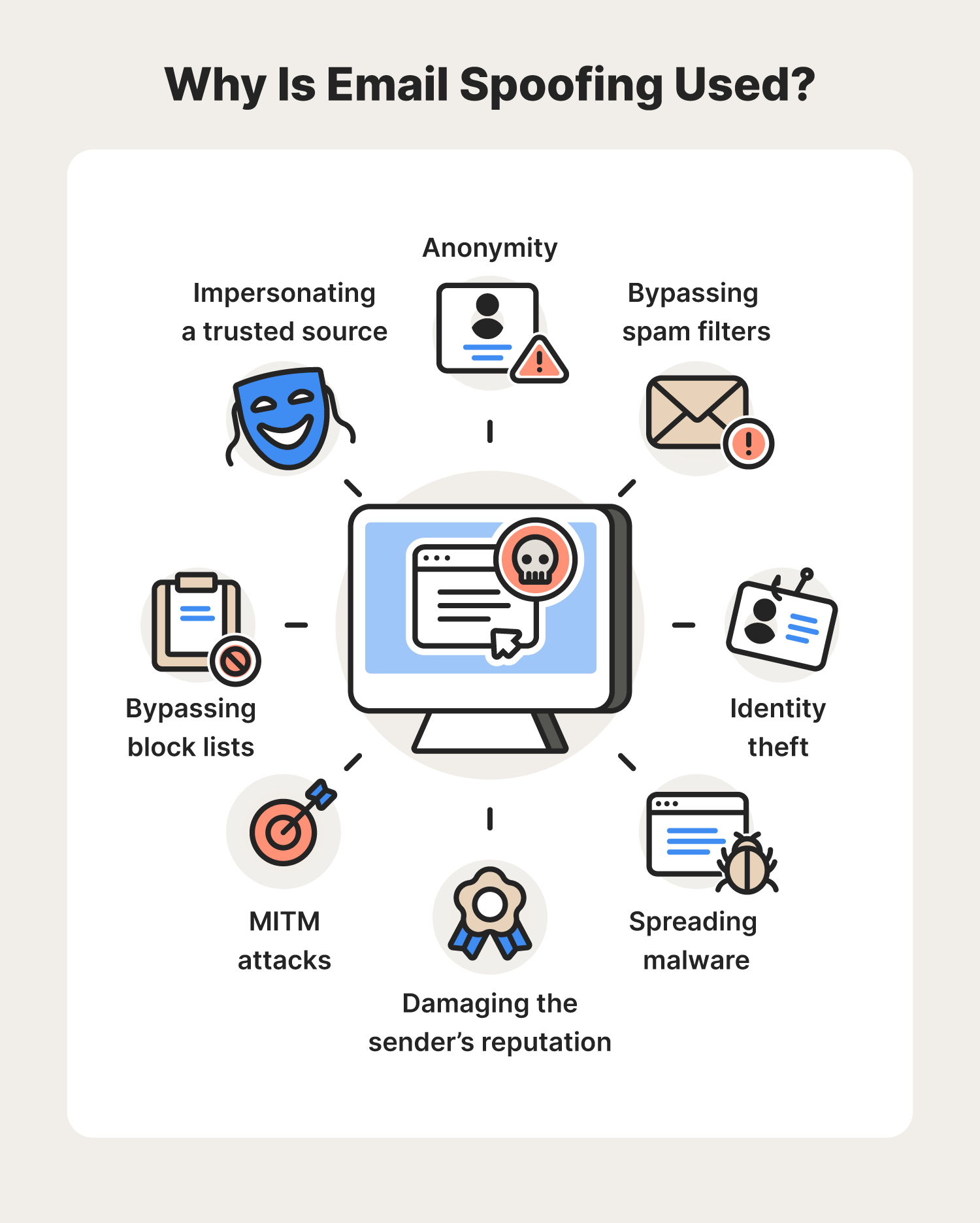
Why is spoofing used?
Spoofing can be used to gain access to a target's personal information, spread malware through infected links or attachments, bypass network access controls, or redistribute traffic to conduct a denial-of-service attack.
How is spoofing used?
Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware. Spoofing attacks come in many forms, including: Email spoofing. Website and/or URL spoofing.
What is spoofing and phishing Class 9?
Definition. Spoofing is an identity theft where a person is trying to use the identity of a legitimate user. Phishing is where a person steals the sensitive information of user like bank account details.
What is the most common method used by cybercriminals?
Phishing: The most popular scam of cybercriminals. The methods used by cybercriminals are becoming more and more advanced and are causing more damage to victims every year.
Is spear phishing the most common?
A definition of spear-phishing This is the most successful form of acquiring confidential information on the internet, accounting for 91% of attacks.
What is the most common motivation of phishers?
The most prominent consequence of phishing is financial loss. Scammers commit financial theft through ransomware attacks, extortion and fraudulent funds transfer. This is usually the motive of a phishing attack that results in a business email compromise (BEC) or ransomware attack.
What is the most common used method for phishing?
1. Email phishing. Most phishing attacks are sent by email. The crook will register a fake domain that mimics a genuine organisation and sends thousands of generic requests.
Why is it called smishing?
Smishing is a social engineering attack that uses fake mobile text messages to trick people into downloading malware, sharing sensitive information, or sending money to cybercriminals. The term “smishing” is a combination of “SMS”—or “short message service,” the technology behind text messages—and “phishing.”
What is phishing and its type?
Phishing is a type of cybersecurity attack during which malicious actors send messages pretending to be a trusted person or entity.
What is a common whaling phishing technique?
Whaling is a highly targeted phishing attack – aimed at senior executives – masquerading as a legitimate email. Whaling is digitally enabled fraud through social engineering, designed to encourage victims to perform a secondary action, such as initiating a wire transfer of funds.
Which of the following is an example of phishing mcq?
Q. Which of the following is an example of a “phishing” attack? Sending someone an email that contains a malicious link that is disguised to look like an email from someone the person knows.
Which one is phishing?
Phishing is the most common type of social engineering, the practice of deceiving, pressuring or manipulating people into sending information or assets to the wrong people. Social engineering attacks rely on human error and pressure tactics for success.
Where is phishing used?
Phishing can be conducted via a text message, social media, or by phone, but the term ‘phishing' is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive.
What are the different types of identity spoofing?
Identity spoofing is a type of cybercrime that involves impersonating someone else to gain access to their personal information or carry out fraudulent activities. There are different types of identity spoofing, including Email Spoofing, Caller ID Spoofing, IP Address Spoofing, Website Spoofing, and Facial Spoofing.